Know your Visitors - AS207111 Whois
In this article, I'll go over the new Whois service and how to make the most of the VPN detection feature. I have divided the story into the following areas: The History About AS207111, About the Whois Service, Getting Started, How To Deal With VPNs, Hosters and IP Bans and a Conclusion
The History About AS207111
AS207111 was created in 2016, during my training as an IT specialist. I had successfully participated in the Network+ certification and had a strong interest in BGP routing of IPv4 and IPv6 addresses. Through a colleague at work I was able to apply for my own AS number.
For some years I did nothing with the network, but now I brought the Whois service to life again. Actually the Whois Service should be a Looking-Glass, but the name Whois fit better to the service.
The Whois Service
Over the past few weeks, I have spent some time developing a intelligent system for detecting VPN traffic. For Proxy, VPN or Tor exit address detection, I use machine learning and probability theory techniques using large datasets from multiple sources with 11,500+ networks from 2,200+ privacy providers. These can be AS numbers, IP blocks, usage type or other vectors.
With our own AS number we have access to the routing tables of the Internet and can therefore receive updates of IPv4 and IPv6 traffic in real time.
Getting Started
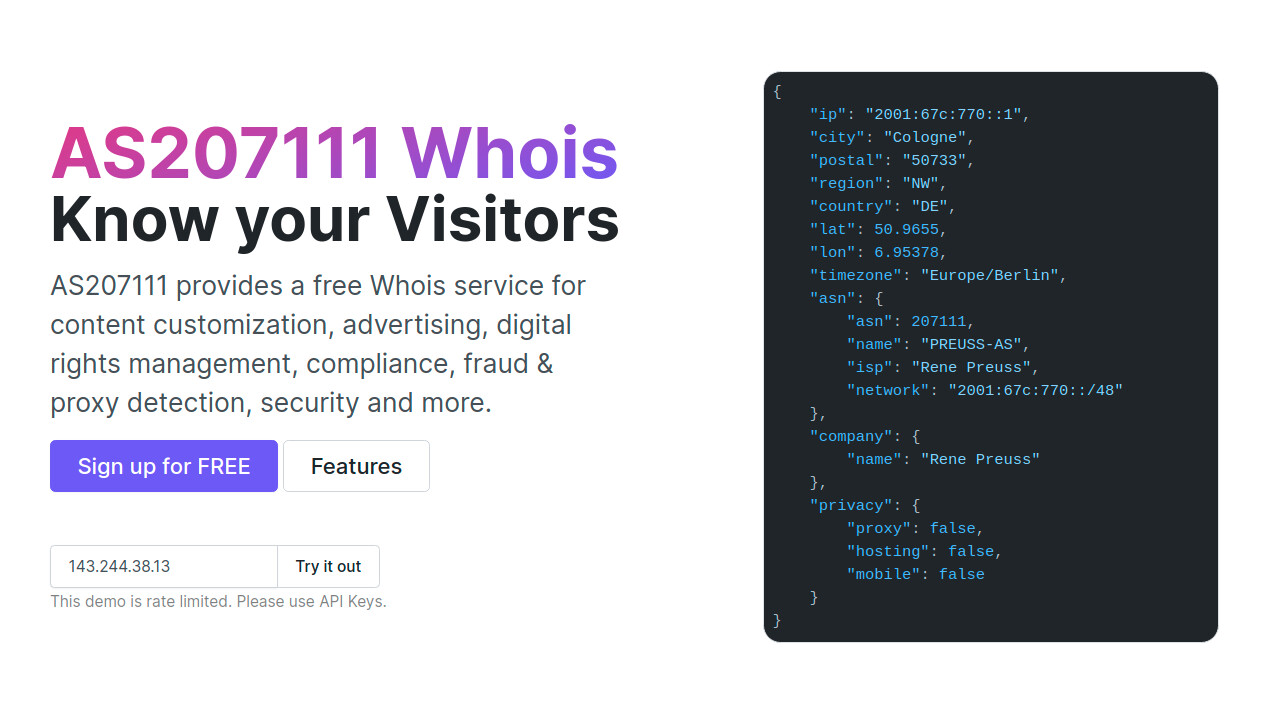
First you need to generate an API token on whois.as207111.net, with this you have access to all premium features, such as the premium proxy, VPN or Tor exit address detection, for free. In the future we will also integrate the cybercrime feeds. These will give more information about the usage type of the IP address.
Next, you can easily use one of our API clients from NPM or Composer. Here in the example we use NodeJS:
Important: I recommend to use the client only in the backend. If the Access Tocken is public exposed, we will revoke your API Access Token.
const whois = require('@as207111/whois');
// You can specify config defaults that will be applied to every request.
// whois.defaults.accessToken = 'your-api-access-token';
whois
.lookup({ip_address: '2001:67c:770::'}, {
// You can override defaults in the options parameter (optional)
accessToken: 'your-api-access-token',
})
.then(response => console.log(response.data));
In the background the following API request is made:
GET https://whois.as207111.net/api/lookup?ip_address=2001:67c:770::
Accept: application/json
Authorization: Bearer <your-api-access-token>
Which gives us the following API response in the resolved promise:
{
"ip": "2001:67c:770::1",
"city": "Cologne",
"postal": "50733",
"region": "NW",
"country": "DE",
"lat": 50.9655,
"lon": 6.95378,
"timezone": "Europe/Berlin",
"asn": {
"asn": 207111,
"name": "PREUSS-AS",
"isp": "Rene Preuss",
"network": "2001:67c:770::/48"
},
"company": {
"name": "Rene Preuss"
},
"privacy": {
"proxy": false,
"hosting": false,
"mobile": false
}
}
That's it.
How To Deal With VPNs & Hosters
If you want to restrict your system from VPNs, then I recommend excluding proxy and hosting traffic. Background: Why would a normal user want to visit your website through a hoster (datacenter).
Sometimes it can take a while until we recognize hoster IPs as VPN addresses. Because many VPN providers also use SSD VPS providers like Vultr, Hetzner or AWS. Only some big VPN providers like Private Internet Access use their own ASNs e.g. CDN77.
Furthermore I recommend not to ban the users directly but to flag them and if necessary to work with shaddow bans. Unless it is about avoiding geolocation prices.
How To Deal With IP Bans
With IPv4, it is sufficient to block individual IP addresses. Since we have too few IPv4 addresses that each customer gets several addresses.
With IPv6 it looks different: Typically, an ISP assigns a /64 or smaller subnet to establish service on the WAN. A /64 is a standard size IPv6 subnet as defined by the IETF. An additional network is routed for LAN use.
With IPv6 it is worth to blocck /64 CIDR addresses. This is the address defined within asn.network. Example: My IP address is 2001:67c:770:6360:cd91:9bb2:1f28:bb4. I have assigned the block 2001:67c:770:6360::/64 on the WAN. That are 18,446,744,073,709,551,616 IPv6 addresses available for my computer to change.
Reference: IPv4 & IPv6 CIDR Chart
Conclusion
In this post we learned how to integrate the Whois service and how to deal with IPv6 bans and what my recommendations are for IP bans.
Furthermore, you can see that IPv6 bans are much more complex and Whois services can help to better exclude networks, because in the Whois response contains ASN network information for that case.
Related stories
With SUBtember right around the corner, you might be wondering what all the fuss is about. What's the difference between a subathon and SUBtember? Let's take a closer look.

Düsseldorf. 70,000 visitors came to the DoKomi for manga fans and cosplay in Düsseldorf. This means that DoKomi set a new record for visitor numbers and a growth of +27 percent (compared to 2019).
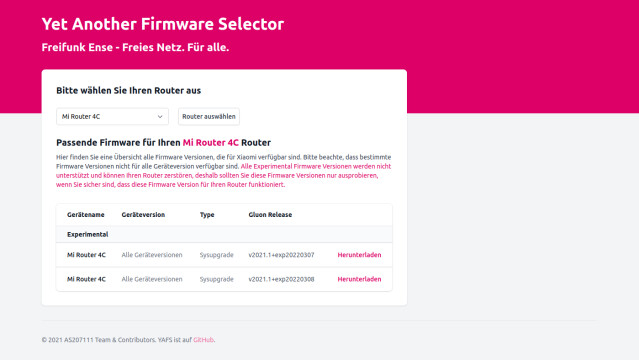
Mit YAFS (Yet Another Firmware Selector) ist es nun möglich die Freifunk Ense Firmware für unterstützte Router zu finden und herunterzuladen.